I recommissioned a Cisco 4503 switch today with a SUP II+TS and whenever I get the chance to wipe a switch or device and start fresh I like to upgrade the IOS and ROMMON if applicable. This procedure was slightly different from a Router ROMMON upgrade:
! Copy the ROMMON image to the bootflash:
Switch#copy ftp://192.168.1.1/cat4500-ios-promupgrade-122_31r_SGA4 bootflash:cat4500-ios-promupgrade-122_31r_SGA4
! Once copied, reload the switch
Switch#reload
! Press Crtl-C to enter ROMMON during bootup and run the following command
rommon 1 > boot bootflash:cat4500-ios-promupgrade-122_31r_SGA4
After the ROMMON upgrade has completed, the switch wil reload automatically and boot into IOS. You can perform a show version to verify that the ROMMON has been upgraded.
More detailed instruction can be found in the Release Notes of the ROMMON image.
Wednesday, August 21, 2013
Monday, August 19, 2013
Zone Based Firewall Example, Part 2 - Guest Zone
Zone Based Firewalls (ZBF) are an easy way to turn your Security licensed Cisco ISR G2 Router into a firewall. In this multi-part example, I'll create a 5 zone firewall which will include an Inside, Outside, DMZ, Guest and Self zones. This is a basic example to demonstrate the the structure of a ZBF, not a study in firewall design.
Just to clarify:
DMZ - Your Demilitarized Zone for web servers and FTP servers
Guest - Wireless guest access to outside
Inside - Your inside LAN
Outside - Represents the Internet
Self - This is the router itself, traffic generated by the router and traffic destined to the router, e.g. TACACS+, SSH, Telnet, TFTP, etc.
In Part 2, we'll look at creating a simple guest wireless network which will allow users connected to the Guest wireless to access the Internet, but not the inside LAN.
! Define Zone for Zone Based Firewall
! Assign Zone to router interfaces
Just to clarify:
DMZ - Your Demilitarized Zone for web servers and FTP servers
Guest - Wireless guest access to outside
Inside - Your inside LAN
Outside - Represents the Internet
Self - This is the router itself, traffic generated by the router and traffic destined to the router, e.g. TACACS+, SSH, Telnet, TFTP, etc.
In Part 2, we'll look at creating a simple guest wireless network which will allow users connected to the Guest wireless to access the Internet, but not the inside LAN.
! Define Zone for Zone Based Firewall
Zone security GUEST
! Class-Map that matches criteria specified in the GUEST-TO-OUT-ACL
Class-map type inspect GUEST-TO-OUT-CLASS
Match access-group name GUEST-TO-OUT-ACL
Match access-group name GUEST-TO-OUT-ACL
! Policy-Map to inspect inside traffic going outbound, dropped traffic is logged
Policy-map type inspect GUEST-TO-OUT-POLICY
Class type inspect GUEST-TO-OUT-CLASS
Inspect
Class class-default
Drop log
Class type inspect GUEST-TO-OUT-CLASS
Inspect
Class class-default
Drop log
! Create Zone Pair and Apply Service-Policy (Policy-Maps)
Zone-pair security GUEST-TO-OUT source GUEST destination OUTSIDE
Service-policy type inspect GUEST-TO-OUT-POLICY
Service-policy type inspect GUEST-TO-OUT-POLICY
! Assign Zone to router interfaces
Interface GigabitEthernet0/2
Zone-member security GUEST
! ACL allows GUEST network to access the Internet
ip access-list extended GUEST-TO-OUT-ACL
permit ip 172.16.0.0 0.0.0.255 any
permit ip 172.16.0.0 0.0.0.255 any
Cisco IP Phone Firmware Downgrade Issue
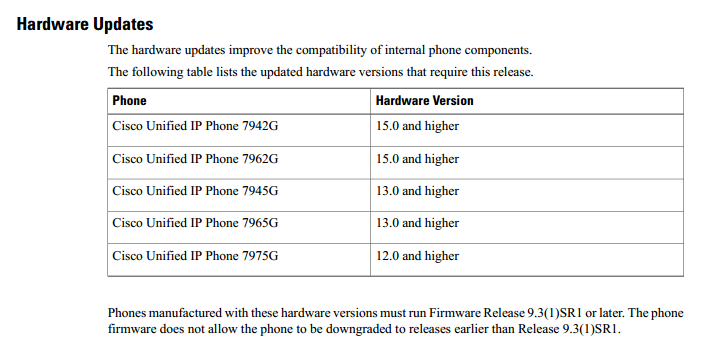
During a Cisco 7965G IP Phone install, I noticed that the phone would download the firmware from the Cisco Unified Communications Server (CUCM), but would not actually install the firmware. The 7965 had a newer load, 9.3(1)SR1, and I was attempting to downgrade to 9.2(3) because of the limitation of the Cisco Phone Designer software. After several reboots of the IP Phone and tinkering with the FTP Services on the CUCM, I proceeded to open a TAC case with Cisco to see if they could solve the issue. After three weeks of packet captures, CUCM log dumps, and even video recording the events, we discovered that the 7965 hardware version that I had (v14) only worked with 9.3(1)SR1 and above. This is clearly stated in the Release Notes for 9.3.(1)SR1, so it just goes to show, don't ignore the Release Notes.
Wednesday, March 20, 2013
Zone Based Firewall Example, Part 1 - Inside/Outside Zones
Zone Based Firewalls (ZBF) are an easy way to turn your Security licensed Cisco ISR G2 Router into a firewall. In this multi-part example, I'll create a 5 zone firewall which will include an Inside, Outside, DMZ, Guest and Self zones. This is a basic example to demonstrate the the structure of a ZBF, not a study in firewall design.
Just to clarify:
DMZ - Your Demilitarized Zone for web servers and FTP servers
Guest - Wireless guest access to outside
Inside - Your inside LAN
Outside - Represents the Internet
Self - This is the router itself, traffic generated by the router and traffic destined to the router, e.g. TACACS+, SSH, Telnet, TFTP, etc.
In Part 1, we'll create the foundation of our ZBF, the inside and outside zones which will allow your users to access the Internet and allow ICMP traffic into your LAN.
! Define Zones for Zone Based Firewall
! Policy-Map to deny all traffic
! Assign Zones to router interfaces
Just to clarify:
DMZ - Your Demilitarized Zone for web servers and FTP servers
Guest - Wireless guest access to outside
Inside - Your inside LAN
Outside - Represents the Internet
Self - This is the router itself, traffic generated by the router and traffic destined to the router, e.g. TACACS+, SSH, Telnet, TFTP, etc.
In Part 1, we'll create the foundation of our ZBF, the inside and outside zones which will allow your users to access the Internet and allow ICMP traffic into your LAN.
! Define Zones for Zone Based Firewall
Zone
security INSIDE
Zone
security OUTSIDE
! Class-Map that matches criteria specified in the IN-TO-OUT-ACL
Class-map type inspect IN-TO-OUT-CLASS
Match access-group name IN-TO-OUT-ACL
! Class-Map that matches criteria specified in the OUT-TO-IN-ACL
Class-map type inspect OUT-TO-IN-CLASS
Match access-group name OUT-TO-IN-ACL
! Policy-Map to inspect inside traffic going outbound, dropped traffic is logged
Policy-map type inspect IN-TO-OUT-POLICY
Class type inspect IN-TO-OUT-CLASS
Inspect
Class class-default
Drop log
! Policy-Map to pass (not inspect) outside traffic coming in, dropped traffic is logged
Policy-map type inspect OUT-TO-IN-POLICY
Class type inspect OUT-TO-IN-CLASS
Pass
Class class-default
Drop log
! Policy-Map to deny all traffic
Policy-map type inspect DENY-ALL-POLICY
Class class-default
Drop log
! Create Zone Pairs and Apply Service-Policies (Policy-Maps)
Zone-pair security IN-TO-OUT source INSIDE destination OUTSIDE
Service-policy type inspect IN-TO-OUT-POLICY
Zone-pair security OUT-TO-IN source OUTSIDE destination INSIDE
Service-policy type inspect OUT-TO-IN-POLICY
! Assign Zones to router interfaces
Interface
GigabitEthernet0/0
Zone-member security INSIDE
Interface
GigabitEthernet0/1
Zone-member security OUTSIDE
!
ACL allows inside network to access the web and to
allow pings to the outside
Ip
access-list extended IN-TO-OUT-ACL
Permit tcp 10.10.1.0 255.255.255.0 any eq www
Permit icmp 10.10.1.0 255.255.255.0 any echo
!
ACL allows pings from the outside to the 10.10.1.0 network
Ip
access-list extended OUT-TO-IN-ACL
Permit icmp any 10.10.1.0 255.255.255.0 unreachable
Friday, February 15, 2013
Cisco Router ROMMON Upgrade
Besides keeping your IOS code up to date, you may want to also update your router's ROMMON version. The first thing to do is download the ROMMON image from Cisco for you specific router. Once downloaded, you'll need to place it in your TFTP server folder so that it can be downloaded by your router. Next, go to your router and type in the following command:
Router#upgrade rom-monitor file tftp://192.168.30.10/C2800NM_RM2.srec.124-13r.T11
You should change C2800NM_RM2.srec.124-13r.T11 to the actual file name that you downloaded from Cisco. Execute the command, the router will download the image and prompt you to allow it to reboot.
Router#upgrade rom-monitor file tftp://192.168.30.10/C2800NM_RM2.srec.124-13r.T11
This command will result in a 'power-on reset' of the router!
System configuration has been modified. Save? [yes/no]: no
Now Reloading
Select Yes and the router will erase the current boot flash and program the new image and reload.
Router#upgrade rom-monitor file tftp://192.168.30.10/C2800NM_RM2.srec.124-13r.T11
You should change C2800NM_RM2.srec.124-13r.T11 to the actual file name that you downloaded from Cisco. Execute the command, the router will download the image and prompt you to allow it to reboot.
Router#upgrade rom-monitor file tftp://192.168.30.10/C2800NM_RM2.srec.124-13r.T11
Loading C2800NM_RM2.srec.124-13r.T11 from 192.168.30.10 (via
GigabitEthernet0/0): !!!!!!!
[OK - 1626367 bytes]
This command will result in a 'power-on reset' of the router!
Continue? [yes/no]: yes
System configuration has been modified. Save? [yes/no]: no
ROMMON image upgrade in progress.
Erasing boot flash
eeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeee
Programming boot flash ppppppppppp
Now Reloading
Select Yes and the router will erase the current boot flash and program the new image and reload.
Subscribe to:
Comments (Atom)